
Freedom of Speech at Risk in Cyberspace
the Electronic World
|

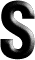
ally, new to the executive level at her company, is on a business trip. It is late at night when she arrives at her hotel. A frequent credit card user, she tries to check in with a Visa card. But the card is over her credit limit and the hotel won’t accept it. Bewildered, she tries Mastercard, then another—all to no avail. She is stranded in a hotel which will not check her in.
She later learns that her credit cards had been “banged” by hackers who obtained her card numbers through the Internet.
When finally tracked down, the ringleader, known as “Agent Steal,” claims it was a simple prank—”my own kind of freedom of expression.”
A freak aberration in the world of the Internet? Unfortunately not.
Take Robert, a software development programmer in Santa Monica, California. Working from his home, he makes his living producing programs for business applications.
One morning he sits down to put the finishing touches on a new program which should save office accountants hours of time each week.
But when he logs on, he finds “black flags”—small but unmistakable signs that his computer has been electronically broken into. He is frantic but has no viable way of finding out what has happened, nor the consequences.
A piece of anonymous e-mail tells the story: a skilled hacker broke into his computer—which was linked to the Internet—and posted his newly completed program onto a “freeware” computer bulletin board, where users can “visit” and download software programs free of charge.
The effect is obvious: months of work—work which he was doing to earn his next paycheck—may just as well have never happened. Adding further insult to injury, the hacker announces that he will send the program to other freeware boards across the world.
Robert responds and asks the hacker why he did what he did—had the hacker somehow been wronged or offended by him? Does he profit from purloined programs?
“No,” the hacker responds to both inquiries. He says that Robert’s problem is that he is one of the “elite” who does not recognize that inherently “all information wants to be free.” And, finally, the hacker explains that disseminating software programs is just his exercise of his “freedom of speech.”
These true stories—the victims requested their names be withheld to avoid provoking further hacker attacks—illustrate a gathering storm in cyberspace. Cyberspace break-ins and piracy have already reached epidemic proportions. It is estimated that as much as 50 percent of the software in use today is stolen or pirated.
Theft by any other name
Freedom of speech is a bogus excuse for a crime. The judiciary should be on the front lines of differentiating between theft and valid free speech matters. But many courts of law are willing to turn a blind eye or to let misplaced concern over possible “chilling” of the First Amendment—even when the First Amendment is no part of the matter—justify letting criminal acts go unpunished.
Case in point: David LaMacchia of Boston operated an electronic bulletin board from Massachusetts Institute of Technology and encouraged users from around the world to copy more than $1 million in software purloined by others from Microsoft, Excel and other software producers.
The losses to software producers and distributors were enormous, irreparable and continuing. LaMacchia’s acts effectively destroyed the value of scores of programs.
With LaMacchia facing criminal charges, his lawyer argued that his client’s conduct could in no wise be deemed criminal as he did not profit personally from scattering the costly computer programs free of charge.
But he also argued that the First Amendment permitted—even encouraged—this criminal conduct. LaMacchia effectively argued that, under the First Amendment, ownership and property were meaningless concepts.
LaMacchia beat the charges and the case was dismissed.
The judge on the case, U.S. District Judge Richard G. Stearns, expressed disapproval of LaMacchia’s conduct, but complained that his hands were tied by a lack of existing laws. “If the indictment is to be believed, one might at best describe LaMacchia’s actions as irresponsible, and at worst as nihilistic, self-indulgent, and lacking in any fundamental sense of values,” he said. But he stopped short of calling it what it truly was: an otherwise criminal act committed with constitutional air-cover.
Whether viewed as a case of judicial weakness or prosecutorial failure, LaMacchia’s case stands as an ominous precedent.
With this logic, a thief could rob a bank, give the stolen money to others, claim his theft was his “statement” against the bank and thus sheltered by the First Amendment, and gain acquittal.
Robert Kruger, director of enforcement for Business Software Alliance, a Washington, D.C.-based group representing major software makers, and a former federal prosecutor, says, “It is just flat-out theft. You are taking someone’s hard work and reproducing it without compensation.”
And in some cases, the courts are willing to recognize this fact. In March 1995, the same federal court sentenced Richard Kenadek, who committed nearly identical acts, to two years’ probation and ordered him to forfeit all equipment related to his bulletin board service. Kenadek, like LaMacchia, made software available on his bulletin board service, but unlike LaMacchia, he charged fees to users—and raised no “First Amendment” defense.
Winn Schwartau, author of Information Warfare, analyzed the effects of such conduct on the business world: “If you invest five years and $1 billion in a new invention, either a product or process, you hope to make a profit on that investment. If, however, I can steal the knowledge to make that product, say for $10 million, I can sell the same item for substantially less and bring it to market in months instead of years. You invest the time and the money, I steal the results, then we compete. Who’s got the advantage?”
Lack of personal restraint by some computer users and lack of effective legal restraint, has led to runaway abuse. “For every one computer break-in you become aware of, there are another 399 break-ins you don’t know about,” said Schwartau.
Attorney and author Lance Rose supports strong law enforcement action against infringers. “They’re doing their job in reminding corporate America that just because it’s easy to copy doesn’t mean it’s legal,” he said.

